Yet, the current situation shines a spotlight on the importance of enterprise risk management (ERM) and the related disciplines of business continuity, disaster recovery and crisis management. Hypotheticals and risk models are being put to the test like never before, bringing any limitations into stark relief.
With many organizations around the globe forced to quickly shift the majority of employees to a work-from-home model — opening themselves up to a whole host of cyberthreats in the process — it’s clear that security and risk management leaders need a more prominent role in shaping enterprise risk management strategies.
This is not news. McKinsey tackled the topic in a November 2018 article, which states:
- “Many CISOs and CIOs would like to integrate their vantage points more deeply into the enterprise risk process, and the risk function can and should be better involved in cybersecurity. However, best practices for achieving risk’s optimal role in identifying, prioritizing, and managing cyberrisk have only begun to emerge. Many companies have struggled to define and distinguish the duties of all relevant parties clearly and logically, so that they can interact effectively and in the right sequence to actually reduce risk.”
If you consider any of the following risk categories commonly identified in ERM plans, it’s no great leap of logic to see how cybersecurity factors into each:
- Strategic and reputational: The threat of not achieving an organization’s objectives, increased competition, limited product innovation/acceptance, lack of responsiveness to industry changes or damage to the agency’s reputation, all of which may negatively impact the organization’s performance.
- Operational: The threat of ineffective and inefficient operations, which may result in security breaches, poor performance, low profitability and the inability to safeguard resources against loss.
- Financial: The threat of an economic crisis and/or poor financial performance, which can negatively impact budget allocations and resource management. Additionally, ineffective internal controls may lead to material misstatements occurring in performance reports.
- Legal and compliance: The threat of the lack of adherence to relevant laws and regulations, which may result in fines, penalties and other legal actions.
- Human resources (people and culture): The threat of insufficient talent, high turnover and inappropriate organizational culture, which may impact the organization’s ability to achieve its objectives.
How COVID-19 is changing the way we think about risk
In a situation like the one we’re facing now, in which your attack surface is shifting seemingly overnight, it is unrealistic to expect that 100 percent of your controls will persist or remain intact. As organizations respond to COVID-19 by embracing a work-from-home model, a plethora of end-user devices are suddenly connecting to business systems via previously untested and potentially insecure consumer routers and home networks. In recent weeks, remote desktops have shifted in importance from a nice-to-have offering for a select group of workers to an essential tool used by wide numbers of employees to keep the organization running. Personal devices and applications are suddenly being used to connect with core business systems.Ensuring security controls of the equipment and systems that enable your organization’s business continuity and disaster recovery plans is absolutely necessary. When you shift the attack surface outside of your traditional boundaries, whether technological or physical, your controls must be able to move with that shift — and do so seamlessly.
CISOs, CSOs and other cybersecurity leaders are uniquely suited to taking on a bigger role in enterprise risk management. Our work puts us squarely in the intersection of technology and business. We have visibility into all of the systems, equipment and processes required to deliver on a business continuity and disaster recovery plan. Being involved in ERM can also make your job a little more manageable: If you can understand all of your systems from a broad enterprise risk perspective it will only make you stronger in cyber as well.
There’s also a clear operational benefit to be gained from performing enterprise risk management exercises. What is revealed in the process will help the entire organization understand how to best prioritize resources — both human and financial — to keep the enterprise running even during a crisis. At a time when organizations are facing a potentially lengthy period of economic uncertainty, it becomes more critical than ever to prioritize investments based on risk.
But cybersecurity leaders can’t perform ERM in a vacuum. Developing a comprehensive enterprise risk management plan requires buy-in from agency executives, and it demands cross-functional collaboration.
Getting started on your enterprise risk management plans
So, where do you begin?The first phase in developing an enterprise risk management strategy is to conduct a business impact analysis (BIA) on all of your systems and processes. The goal is to determine which critical systems and business processes your organization can least afford to live without. The results of the BIA can be used to inform the risk assessment process.
These six steps will help with your initial risk identification and assessment:
- Develop and distribute a risk survey to key stakeholders. These are typically fielded to the senior director level and above and should include representatives from all of the major departments in your organization, including finance, legal, human resources, information technology, information security, operations and communications. Once your survey is complete, you’ll want to organize the responses into risk categories so you can compile an inventory of enterprise risks.
- Conduct research and analysis to compare your organization’s enterprise risks to industry risk surveys.
- Develop a risk assessment methodology, including probability and impact risk rating criteria.
- Identify key leaders in your organization and devote time to interviewing them to get their feedback on risks and prioritization as well as risk probability and impact.
- Present your risk assessment results to executives to finalize the top risks and assign executive risk owners.
- Work with executive risk owners to identify risk mitigation activities for the top risks.
Understanding your systems based on this type of business risk calculus not only serves as the foundation for your cybersecurity strategies, it becomes essential as you build out your business continuity, disaster recovery and crisis management playbooks. You’ll emerge with a list of your most critical processes, making it possible to clearly prioritize responses in a time of crisis — regardless of whether the crisis results from a cyberattack, a natural disaster or a global pandemic.
It’s impossible to prepare for and manage against every possible issue, so having a list of five or 10 enables you to identify the activities you are currently performing to mitigate your risk as well as develop future planned activities. These can serve to help you develop a set of key risk indicators (KRIs) which can then be used to set and communicate key performance indicators (KPIs), enabling you to effectively communicate with executives and key leaders.
If you’re lucky enough to have performed these enterprise risk assessment exercises prior to COVID-19, you would have already thought through how to enable workers at home and how to protect them. Yet, as predictable as the current pandemic may have seemed to some experts, the lack of preparedness evidenced by governments and corporations around the globe leaves us to speculate that very few organizations invested the time and resources to prepare.
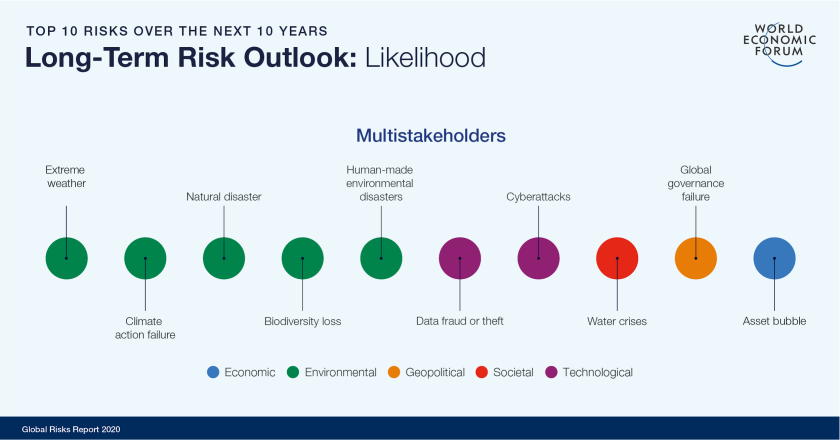
When considered in terms of potential impact, infectious diseases appear alongside cyberattacks, climate action failure, information infrastructure breakdown and weapons of mass destruction in the list of top 10 risks over the next 10 years, according to the World Economic Forum’sGlobal Risks Report 2020, released in January 2020. Yet, when considered in terms of likelihood in the next 10 years, infectious diseases drop out of the list of top 10 global concerns.

A more recent study, the Global Business Barometer, produced by the Economist Intelligence Unit and sponsored by SAS, paints a very different picture. The study is based on a survey of 2,758 executives in 118 countries fielded March 26 - April 6, 2020. When survey respondents were presented with a list of selections of the “most significant challenges” to their business over the next three months, 72 percent picked “an escalation of the COVID-19 pandemic.” Evergreen corporate concerns such as protectionism, talent and skills shortages, and cyberthreats and fraud — all of which had been rising ahead of the pandemic — have moved far down the list of top concerns since the COVID-19 outbreak.
In stable times, it’s all too easy for organizations to treat enterprise risk management as a mere checkbox exercise best left to a segregated team of risk professionals. With COVID-19, business, government and technology leaders have found themselves enrolled in a crisis management crash course. It’s up to each of us to take this as an opportunity to re-think our approach to enterprise risk so we’re better prepared for the down times and well positioned to benefit when things are going well.
Learn more about managing your remote workforce. Visit https://www.tenable.com/remote-workforce.
About the Author
Robert Huber, Tenable’s chief security officer, oversees the company's global security teams, working cross-functionally to reduce risk to the organization and its customers. He has more than 20 years of information security experience across the financial, defense, and critical infrastructure sectors. Prior to joining Tenable, Robert was a chief security and strategy officer at Eastwind Networks, where he focused on growing the company’s business and delivering omni-environment security solutions. He was previously co-founder and president of Critical Intelligence, an OT threat intelligence and solutions provider, which cyberthreat intelligence leader iSIGHT Partners acquired in 2015. He also served as a member of the Lockheed Martin CIRT, an OT security researcher at Idaho National Laboratory and was a chief security architect for JP Morgan Chase. Robert is a board member and adviser to several security startups and is an active member of the Air National Guard, serving in a cyber operations squadron supporting federal and state missions.








